Although Facebook is quite well protected, it is still possible to hack someone's account. More precisely, there are many ways to do it. "How to hack a FB account" is a common question, some would like to hack others, and some to protect themselves from hacking.
No matter how well I was protected by FB, most of the methods used today use man as a weak link.
The following is a list of several ways you can hack someone's FB profile, or how I can hack yours. So, read everything and make sure you protect your account enough.
8 ways to hack Facebook accounts
1. Phishing
This method was popular before, now modern web browsers solve this problem on their own. However, that does not mean that it has been eradicated.
Basically, this method involves creating an identical page of a site (in this case it is FB) for the user to be deceived and to log in thinking that he is on the right site. When you enter your data, it is transferred to the attacker's database and the user will not even notice.
Protection:
- Use Chrome that recognizes sites like this
- Always check the URL (is it facebook.com)
2. Keylogger
One popular method is because it is difficult to detect. A keylogger is a tool that an attacker installs on a victim's computer that starts tracking everything he enters via the keyboard. This information is then sent to the attacker via FTP or mail.
Protection:
- Always download programs from verified sites
- Scan USB every time
- Install a good antivirus
- Clean your computer completely of malware from time to time
3. Saved passwords in the web browser
I have personally seen that people often store passwords in a web browser and that is a big problem. When someone sits down at your computer and you haven't locked it, they can simply visit the saved password page and log in to the site.
If the user is using Chrome, these passwords can be easily accessed from this URL: chrome://settings/passwords
Protection:
- Just don't store passwords in a web browser
- Use some tool for that, say LastPass
4. Session Hijacking
This method is no longer used because FB has completely switched to SSL. In essence, the attacker connects to the same network as the victim and simply "steals" the session by simply intercepting traffic. In this way, the attacker can use the attacked FB account without knowing the login information.
Protection:
- Just always make sure SSL (HTTPS) is enabled
5. Phone hacking
Many users remain logged in to their Facebook account on the phone, and if the attacker becomes in possession of the phone, they can also access the FB account. But, he doesn't have to be physically in possession, it is enough to install malicious software and receive data over the Internet.
Protection:
- Put some phone lock method
- Do not install .apk applications from untrusted sites
- When you visit an infected site, do not click on all the ads that pop up
6. DNS Spoofing
If the attacker and the victim are on the same network, the attacker can use this method to redirect traffic to one of his sites. For example, he can redirect to one of his phishing pages and the user will not notice because he knows that he typed facebook.com. This method is also less successful because more modern web browsers have protections.
Protection:
- Use more modern web browsers
- Please check the URL before signing up
- Check the DNS settings in the system
- Check the DNS in the router on your network
7. USB hacking
Some scripts can extract saved passwords from a web browser the moment a USB is inserted into your computer. USB has a lot of vulnerabilities and always be careful who you insert.
Protection:
- Do not buy used USB sticks
- Always scan the USB after inserting it into the computer
8. Man In The Middle (MITM)
It is a popular method and there are even Android applications that use it. In this case, the attacker is placed between the Internet and the user so that all traffic passes through it. In this way, it can save some important data or insert its own.
Protection:
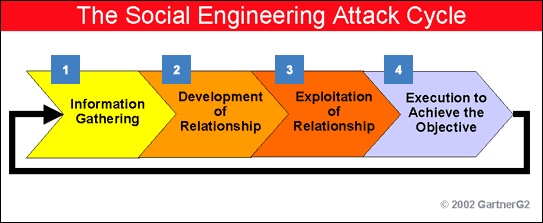
BONUS: Social Engineering
This is the true definition of using man as the weakest link. The attacker simply extracts information from the victim to get a possible password. Users who are not accustomed to technology and use passwords such as children's names, streets, and numbers, place of birth, etc. are easily hacked by this method.
The attacker first impersonates, then befriends the victim, tries to extract some important information, and finally uses combinations to compile a password.
Protection:
- Do not share your personal information
- Avoid suspicious profiles
That would be it for this article, I hope you found it useful.
Disclaimer: You do everything at your own risk. I, or anyone else, is not responsible for any damages and consequences resulting from the use of information and tools from this text.








Comments
Post a Comment