Every person has a unique fingerprint, as well as almost every device through which you visit sites.
Namely, sites can access some information about your system through a web browser and create a digital fingerprint based on that. Later, this information is sold to advertising agencies and they follow you on the Internet and place advertisements.
Of course, this method of identifying individuals on the Internet is also useful because it is easier to find and track criminals, or to detect suspicious reports on, say, bank accounts.
How to create a device fingerprint?
There are two methods used, and they are often used together. I will explain both in the simplest way I can.
Canvas
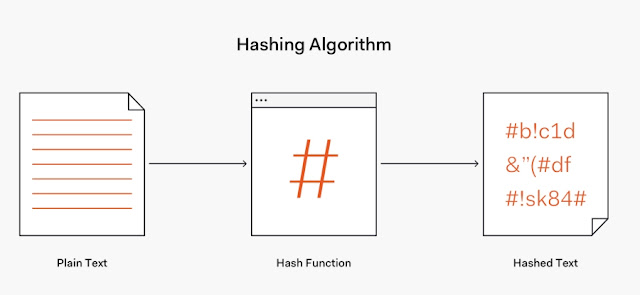
To understand how this method works, I must first explain what hashing is, ie. in English - hashing.
Hashing
Hashing allows you to use certain algorithms to convert some data into a unique compressed string.
For example, the word "tech" has an MD5 hash "D9F9133FB120CD6096870BC2B496805B"
Doesn't work compressed? In this case, it is not because the original data is quite small, only a few letters. But you can hash the whole image, audio file, long text, zip archive… and get one simple string of random characters as a result.
That string is unique! If you change at least one bit in the source data, the hash changes completely.
So, although "on the eye" two pieces of information act identically, the hash will look completely different.
For example, the word "tech " has the hash "DB676F962D9E75F82D625C451D0A36C4". As you can see the only difference in the source information is the space at the end but the hash is completely different. Through the hash, one cannot even guess that there are two almost identical pieces of information.
The other important thing is that you can't extract the original information from the hash. So, hashing only works in one direction.
Canvas fingerprint
This whole hashing story is important because this method is used to save your Canvas fingerprint.
Modern web browsers use the HTML5 standard and come with a Canvas element for drawing on web pages.
Useful: test your Canvas fingerprint.
Basically, with a few lines of code, you can tell a web browser to draw something on the screen, like on a canvas (hence the word canvas).
Now, tracking scripts use the JavaScript language to instruct the web browser to draw something on some invisible Canvas on the web page. You would do the same, but in this case, the scripts do it themselves and you don't see it.

|
| Hash pictures are drawn on Canvas |
These scripts give the web browser the task of drawing a specific image. In that picture, you can find various shapes, text, colors, and lines… and each computer will draw them the same.
Did I write "the same"? No, it will only work the same for us, but not for the computer! And this is the crucial thing when creating a Canvas FP.
Namely, an approximately identical image can differ at the pixel level depending on several factors such as the web browser itself, the version of the web browser, and the graphics processor…
This difference in pixels is what is unique about each device and this is exactly what tracking scripts use.
These scripts convert drawn images on Canvas into one Hash string that is unique, easily transferred to remote servers, and takes up significantly less storage space than the entire image.
Remember that if the original information changes and at least the hash will be completely different? The same is true here: if at least one pixel differs in that Canvas image, the hash will be completely different. If the hash is the same - the image was drawn by the same device.
Example in practice: visit the XYZ online store and that site uses a script from a tracking company. This tracking script instructs your web browser to draw an image. When it does, the script takes the hash of that image. You visit another XYW site that uses the same tracking script and normally the script asks the web browser to draw the same image. Since your computer draws that image in its own unique way the hash will be the same. And now the script on the XYW site knows that you have visited the XYZ site before because the two hashes match.
As you can see, this method does not require users to have cookies enabled, which are otherwise used to track users through sites.
Of course, it happens that someone else in the world has the same graphics card and browser, so the hash matches, but that's why this technique is used in combination with others to identify you even more accurately.
Device info
To narrow the choice of users, tracking scripts use more information that can be accessed very easily.
Namely, the browser has access to a large amount of information about your device such as user-agent, installed fonts, system language, system version, plugins, WebGL data, available and included sensors… the list is too long.

|
| Example of a fingerprint device / amiunique.org |
You visit a site with a script to create a fingerprint and it picks up all that information.
Since there is a lot of information, your computer will likely be unique, because what is the chance that someone else has all this information the same as you?
In fact, research has shown that only 1 in 286,777 web browsers share the same Browser fingerprint.
You can see your fingerprint on this site and find out if it is unique. You can visit the site again after a while, delete cookies and cache, and do a new test. Then open the History page on the site and see if there are previous results. If they are, it means that your fingerprint has not changed and that I can easily follow you on the Internet with this method.
How to protect yourself?
You basically have to give up a lot to hide your digital footprint because you would have to block or randomize all those plugins and APIs you use for regular surfing.
There are various add-ons for web browsers that do it all for you, but the question is whether they also collect information.
The safest and easiest method is to use the Tor web browser. The only downside is that, due to too much security and privacy, you have to wait a little longer while the pages load.
The second best method is the Brave web browser because it has built-in fingerprint protection and I warmly recommend that you install it.

Comments
Post a Comment